Iranian Regime’s Presidency Websites Disrupted, Classified Documents Obtained
iran ghamosarnegouni president.ir
Written by
Mohammad Sadat Khansari
On May 29, a group of Iranian hacktivists under the moniker “GhyamSarnegouni” or “Rise to Overthrow” in Farsi, claimed responsibility for taking down numerous Iranian presidency-affiliated websites.
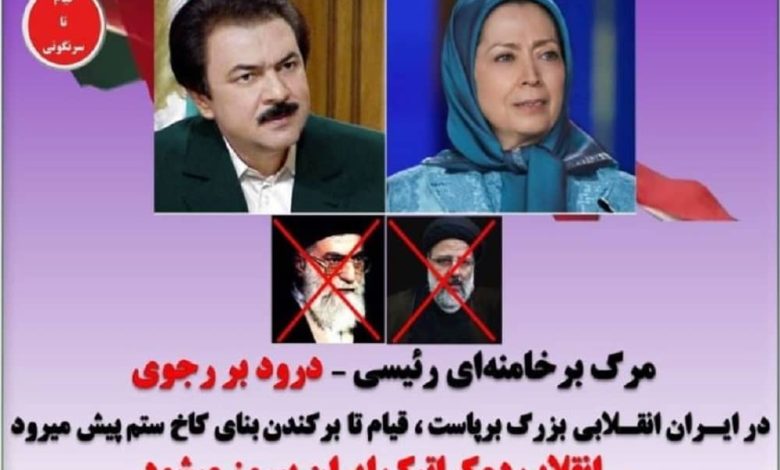
The group dismantled the regime’s digital safeguards and replaced photos of the Iranian regime’s Supreme Leader Ali Khamenei and President Ebrahim Raisi with those of Massoud Rajavi, the leader of the Iranian Resistance, and Maryam Rajavi, the President-elect of the Iranian opposition coalition National Council of Resistance of Iran (NCRI). On other websites, the defaced images of Khamenei and Raisi served as symbols of rejection and dissent.
One targeted site exhibited the slogan, “Death to Khamenei/Raisi! Hail to Rajavi!” “Hail to Rajavi!” This incident follows a preceding disruption of websites linked to the regime’s Foreign Ministry by the same group earlier this month. In that incident, “GhyamSarnegouni” disclosed over 50 terabytes of data extracted from the regime’s Foreign Ministry servers.
The Associated Press reported on Monday that the regime in Iran “has been targeted by a series of embarrassing hacks amid the rising tensions over its rapidly advancing nuclear program. That’s included the signal of Iranian state television being targeted, gasoline pumps that provide subsidized fuel being targeted in a cyberattack, and government surveillance camera imagery being released, including from a notorious prison.”
Secret Deals and Hostage Games: Leaked Documents Unveil Iran’s Attempts to Free Assadihttps://t.co/nJkH2M5RLN
— NCRI-FAC (@iran_policy) May 13, 2023
Despite the deliberate silence from Iranian state media and officials concerning these breaches, the regime finds itself amidst a series of devastating cyber intrusions.
These assaults have targeted critical parts of the regime’s infrastructure, including its prized nuclear program, its state television, and even government surveillance cameras.
The dissidents have furnished comprehensive revelations regarding today’s disruption and defacement of Iranian presidency-affiliated websites. These revelations encompass the acquisition of highly classified documents and the defacement of the following:
The group seized control over a staggering 120 servers within the presidency’s internal network and central databases.
The group successfully gained control over the government’s server management network and server controllers, enabling them to manipulate critical infrastructure.
The group infiltrated the presidency’s network of technical administrators, allowing them to disrupt operations from within.
By breaching the “Users Internal Network,” the group penetrated over 1,300 computers within the presidency’s internal network.
Access was obtained to systems housing classified internal communications associated with the presidency and the government, unraveling their confidential exchanges.
The group managed to breach the encryption system responsible for classified and encrypted messages spanning recent years, exposing sensitive information.
The group obtained entry to tens of thousands of classified, top-secret, and secret documents linked to the presidency. Notably, this included documents concerning the appointment of Ali Akbar Ahmadian as the new Secretary of the regime’s Supreme National Security Council.
Full report on widespread hack of Iran state-run TV and media
The group successfully infiltrated the presidency’s websites and numerous internal applications, enabling them to manipulate and exploit vital platforms.
Access was gained to an array of classified documents, such as the architectural blueprints of Raisi’s office and sleeping quarters, the fiber-optic cable network connecting the presidency to Khamenei’s headquarters, as well as various entities within the mullahs’ regime, including the government cabinet, judiciary, Interior Ministry, Intelligence Ministry, Foreign Ministry, IRGC paramilitary Basij Force, Majlis (parliament), state TV and radio apparatus, Tehran’s airports, and more.
Detailed information was acquired, spanning 19 pages, regarding the technical infrastructure of the presidency’s computer network, fiber-optic network maps, and building patch panels. An additional 21 pages disclosed the technical network’s intricate details, including IP addresses. Furthermore, 104 pages revealed telephone numbers, internal phone systems, and direct lines interconnecting every room within the presidency building.
Classified documents outlining Raisi’s planned foreign trips for 2023 were obtained, encompassing destinations such as Iraq, Syria, Pakistan, Indonesia, Kyrgyzstan, Oman, Uganda, Zimbabwe, Kenya, Venezuela, Cuba, Nicaragua, Uzbekistan, South Africa, India, Shanghai summit, the Caspian Sea summit, Tajikistan, Kazakhstan, the UN General Assembly in New York, Uzbekistan, and Gambia.
The group exposed the identities of the 25-member security team safeguarding Iranian regime First Vice President Mohammad Mokhber.
Highly confidential letters from the IRGC command in Tehran, relating to at least five meetings of the Joint Security-Intel Committee overseeing the crackdown on the country’s universities, were intercepted, shedding light on covert operations.

